
Security Manager
Provides real-time visibility, control, and management for network security devices across hybrid cloud environments from a single pane of glass
- Analyze firewall configurations to identify hidden, unused, shadowed,or overly permissive rules
- Validate policies against regulatory requirements or custom-defined policies
- Isolate, document, and alert on every change to network access
- Simulate patching based on vulnerability type, asset score, and security policy exposure
- Gain full visibility and unified security policy management across your hybrid cloud security controls
The FireMon Security Manager platform provides detailed, customizable network security analytics and real-time assessment of policy enforcement across your hybrid enterprise from an easy-tounderstand, centralized dashboard
AUTOMATION OF MANUAL TASKS
Streamline compliance auditing and validation processes with automation to ensure network access controls are in place at all times
DASHBOARD-DRIVEN USER INTERFACE
Gain real-time visibility and control into devices, complexity and compliance across your enterprise in a single pane of glass
UNPARALLELED IN-DEPTH ANALYSIS
Assess your network security infrastructure using Elastic search for sub-second results
UNMATCHED SCALABILITY
Perform simultaneous analysis and normalization across multiple platforms from multiple vendors, while splitting out reporting functions on a dedicated appliance
UNRIVALED DATA RETENTION
Retain every piece of data received indefinitely without any system performance degradation
COMPREHENSIVE VISIBILITY
Collect live traffic flow data with Traffic Flow Analysis (TFA) that provides greater insight into the applications traversing a particular security rule
REAL-TIME CHANGE ANALYSIS
Know the who, what, and when of every change that happens to monitored devices in real time
NGFW SUPPORT
Support seamless migration for applicationcentric policies for NGFW monitoring, policy
implementation and management systems
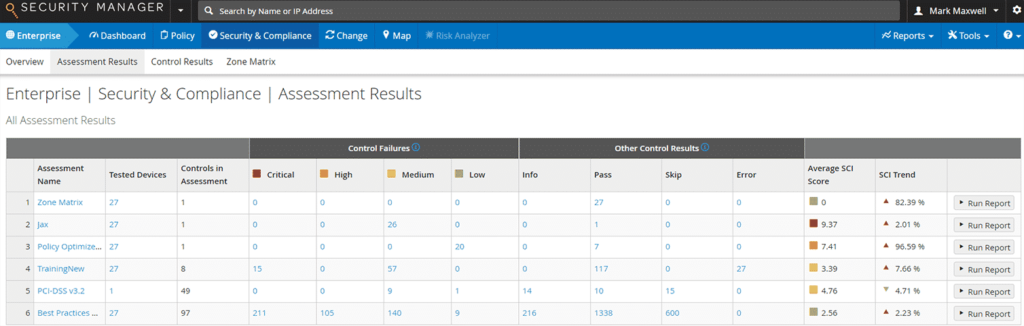
Security Manager provides automated compliance assessment capabilities that help you validate configuration requirements and alert you when violations occur. Whether you need audit reports ready out-of-the-box or customizable reports tailored to your unique requirements, Security Manager reduces the time you spend configuring policies and gives you the confidence that you’re ready to meet your regulatory or internal compliance audit demands.
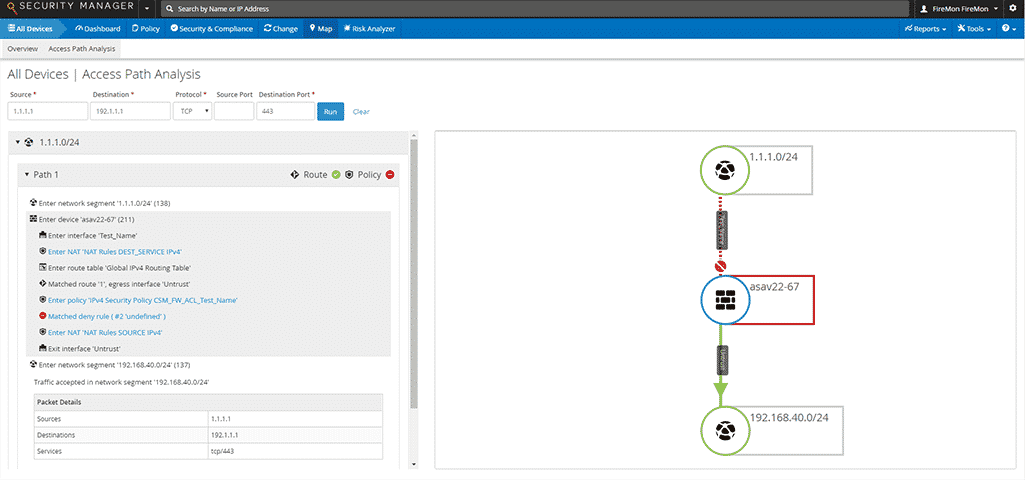
Through real-time traffic flow analysis, Security Manager tracks behavior across your hybrid network to identify which applications are being used in a rule and between sources and destinations. You can also correlate your vulnerability scans with Security Manager’s access path analysis to trace every available access path across the network to effectively reduce your network’s attack surface with a defined path to remediation
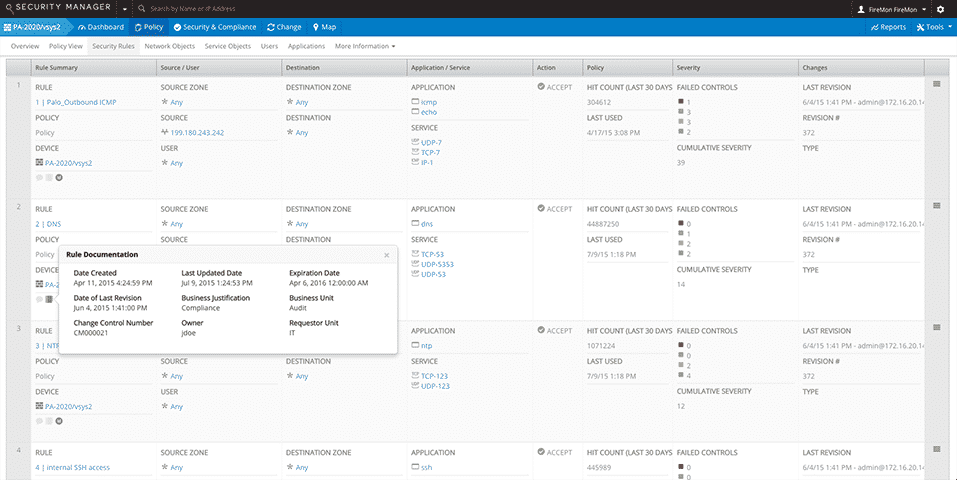
With Security Manager, you can easily create, maintain, and distribute security policies in highly dynamic environments, as well as scope the impact of proposed policy changes on your compliance and security posture. Real-time change analysis documents the who, what, when and why of every change and establishes a baseline for normalized device rules. By automating and orchestrating change management, Security Manager ensures your ability to operate at scale across your cloud, virtual and hybrid environments
Security Manager helps you maintain policies on your network security devices to eliminate unnecessary access and risk. With comprehensive rule analysis and automated workflows for rule review, you can remove technical mistakes and misconfigurations, remove unused access, and review and refine access to optimize the performance of your devices, reduce policy complexity and enhance your security profile
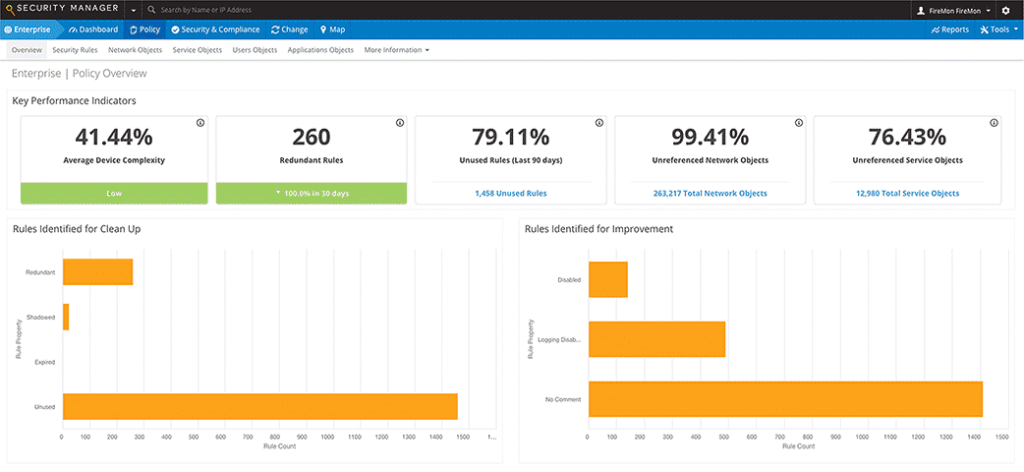
Security Manager’s unmatched scalability, in-depth analysis and third-party integration enables real-time, centralized visibility and control as your hybrid network evolves. You can perform simultaneous analysis and normalization across multiple platforms and vendors while splitting out reporting functions on a dedicated appliance, and retain data indefinitely without any system performance degradation. Our flexible and dynamic API lets you incorporate information you’re your third-party solutions for comprehensive, centralized network security assessment and management.




