Targeted Cyber Intelligence
Darknet monitoring tailored to your organization, detecting threats specifically targeting your key assets
KELA Provides Comprehensive Cyber Intelligence Solutions
We scan the Darknet to identify specific threats targeting our clients. KELA maps the most relevant attack vectors and leak sources, identifying leaked IT systems and topology, employee information, user credentials and product vulnerabilities. The targeted cyber intelligence enables our clients to gain a completely external view of their position and vulnerabilities, designed to prevent data breaches at the earliest possible stage.
What Makes KELA Unique?
KELA gathers, detects, and analyzes intelligence from a curated set of Darknet sources, providing clients with fully targeted intelligence. Our intelligence experts assess and qualify threats, ensuring the intelligence is 100% actionable.
Extreme Targeting
KELA provides intelligence about threats that specifically target your organization. Our clients will never be flooded with general, low-impact threat intelligence, allowing them to focus time and efforts on relevant threats targeting their organizations.
Curated Sources
KELA gathers, detects, and analyzes intelligence from a curated set of Darknet sources, providing clients with fully targeted intelligence. Our intelligence experts assess and qualify threats, ensuring the intelligence is 100% actionable.
Automation & Service
While the process of intelligence gathering is 100% automated, our cyber experts examine and research every incident. When an incident occurs, you want the smartest, most diligent experts to be a part of your team.
What does KELA offer?
Read below to learn more about KELA's proprietary darknet-based solutions. Contact us today to get started!
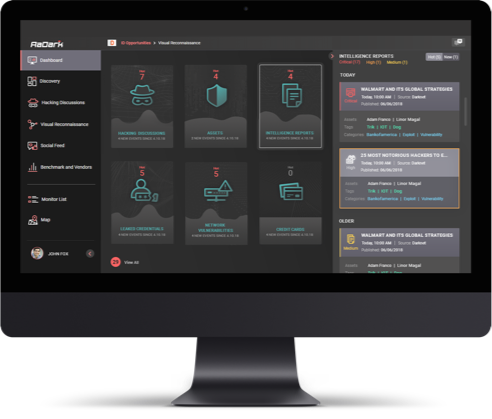
The Radar of the Darknet
RADARK automatically monitors a curated set of Darknet sources to detect users about compromised corporate assets.
The Radar of the Darknet
RADARK automatically tracks Darknet threats, and immediately alerts users about compromised corporate assets – employee or customer details, email addresses, passwords, and much more. Keywords configured in any language and new sources hand-picked by our analysts daily, guarantee that RADARK delivers the most relevant, accurate, and highest quality intelligence.

The Google of the Darknet
DARKBEAST allows our clients to access all types of information available in KELA’s data lake of Darknet sources.
The Google of the Darknet
DARKBEAST enables users to perform in-depth and secured investigations through KELA’s data lake and immediately obtain information on various data points. DARKBEAST’s quick pivoting capabilities allow users to retrieve accurate results from the dark web, open web, and instant messaging platforms such as Telegram & Discord.
While the process of intelligence gathering is 100% automated, our cyber experts examine and research every incident. When an incident occurs, you want the smartest, most diligent experts to be a part of your team.

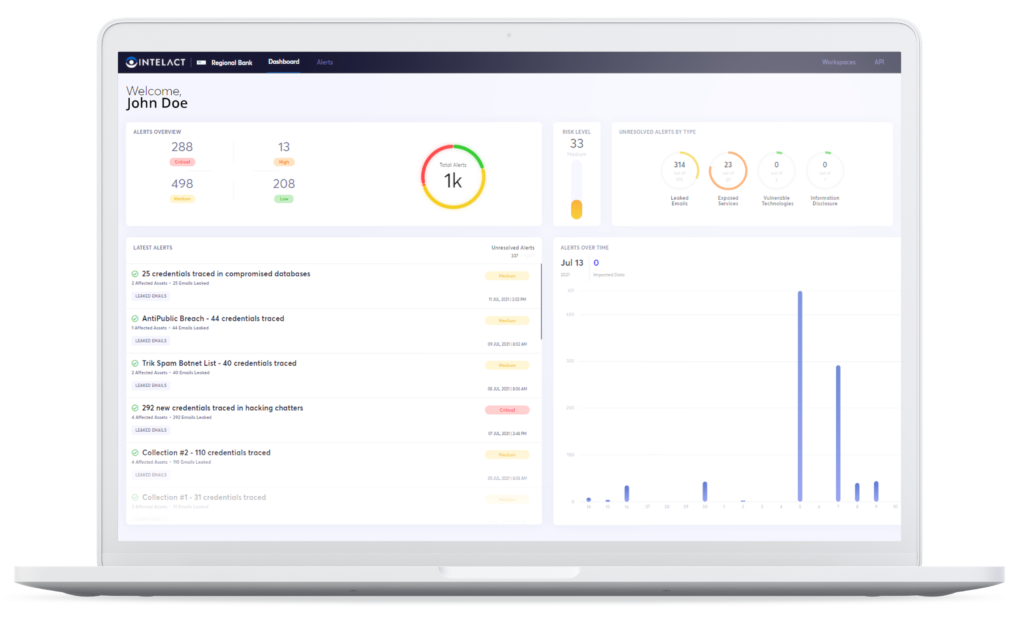
As the underground threat landscape is constantly
evolving, all types of organizations are requiring
solutions for monitoring their assets. IntelAct offers
organizations a fully automated and targeted
solution for Attack Surface Monitoring. IntelAct’s
workspace will enable tailored configuration of
client’s assets, automated monitoring of these assets
in KELA’s Dark Net sources, and real-time alerting on
any compromise or exposure of those assets.
Targeted Threat Intelligence
INTELLIGENCE POINT OF VIEW
KELA’s process of gathering and analyzing data emulates the thought-process of a hacker prior to an attack.
MULTILINGUAL TEAM
While KELA’s technologies monitor intelligence in more than 100 languages, our team speaks a total of more than 20, all common in Darknet communities.
HUNDREDS OF CURATED SOURCES
Our analysts scan and handpick new information sources daily, ensuring all potential threats are being monitored.
TARGETED MONITORING
Highly targeted intelligence-gathering prevents any generic, redundant or low-impact threats.
REAL-TIME ACTIONABLE INTELLIGENCE
Immediate notifications and 100% actionable alerts of Darknet threats.
TECHNOLOGY & ANALYSTS
Integrating automation and manual oversight by analysts guarantees the most relevant intelligence analysis and remediation process.

Dark web based attack surface intelligence for MSSPs
AUTOMATED ATTACK SURFACE INTELLIGENCE
100% automatic delivery of targeted attack surface intelligence
100% automatic delivery of targeted attack surface intelligence
REAL-TIME ALERTS
Proactively take action on intelligence to eliminate immediate risks
TARGETED & ACTIONABLE INTELLIGENCE
Monitor specific assets to receive only targeted and actionable intelligence
Monitor specific assets to receive only targeted and actionable intelligence
MAINTAIN A REDUCED ATTACK SURFACE
Efficient detection of darknet threats helps users maintain a reduced attack surface
Efficient detection of darknet threats helps users maintain a reduced attack surface
SEAMLESS INTEGRATION
Easily integrates with other security technologies
Easily integrates with other security technologies
SIMPLE CONFIGURATION
Simple to use and quick deployment for immediate monitoring of assets
Simple to use and quick deployment for immediate monitoring of assets