
Perimeter81 Webinar
https://youtu.be/UCJs34jVolM Sometimes it isn’t enough to “set and forget” – you need an in-depth view of your networks and policies. The monitoring dashboard from Perimeter81,
Leading Regional VAD Cyber Security and
IT distributor supporting local Channel Partners









https://youtu.be/UCJs34jVolM Sometimes it isn’t enough to “set and forget” – you need an in-depth view of your networks and policies. The monitoring dashboard from Perimeter81,

Phishing attacks and account takeovers are on the rise, yet not all types of multi-factor authentication (MFA) are up to the task of preventing modern

https://youtu.be/mHq1J2r6rSg Your security challenges grow faster than your team. That’s why you need security testing automation built into every step of your SDLC. – Automate

Why an investment in PAM is your best bet to combat cyber attacks https://www.youtube.com/watch?v=gH7boH02jMg Cloud Transformation is Increasing Ransomware Risk according to the latest Cybersecurity

Don’t hesitate to contact us for any inquiry regarding technology or pricing Contact Us Speakers Robin MüllerTechnical ConsultantAnyDesk Revital LawrenceGlobal Marketing ManagerMultipoint Group https://youtu.be/OFWfwYa8qu8 Agenda:11:00

On-Demand Webinar SMART PROTECTION FOR SENSITIVE DATA AND SECURE COLLABORATION Don’t hesitate to contact us for any inquiry regarding technology or pricing Contact Us

The Most Advanced Encryption Software Unique solution that ensure the highest levelof communication confidentiality and anonymity. Tools for encrypted communication, resource encryption, are becoming more and

DETECT THREATS FASTER to avoid being the next breach headline. Join our Live Webinar with experts from NETWRIX and Multipoint Group and learn how to:

Protect your data where you can, monitor for it where you can’t. We’ll discuss how monitoring the surface and the deep Dark Web becomes an

We’d like to personally invite you to our upcoming event, “Enabling the Alternative Cloud”. Experts from Virtuozzo and Multipoint Group will show you how to
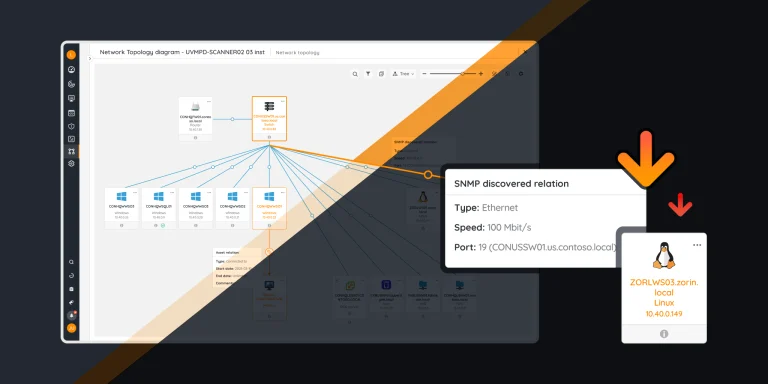
By visualizing the relationships between your IT assets, you can: – Easily spot and troubleshoot issues. – Make informed decisions about changes, upgrades, and maintenance, and
Uncertainty causes stress. That’s why humans have been so afraid of the dark since the beginning of time – we are never sure what’s out

Do you want to increase network performance with no budget nor additional staff? Extend the Life of Existing Tools THE LONGER YOU CAN USE EXISTING

Why We Need to Rethink Cyber Security as We Know It The digital world is changing faster than ever. We are constantly connected online and

What are Social Engineering Attacks? Social Engineering is an act of manipulating people to expose confidential or sensitive information. This can be done by telephone,

Close any Forescout deal worth between €20k and €50k You are eligible to join the club and make a purchase worth between 20k and 50k
Multipoint GROUP is a leading distributor of IT security and Internet technology solutions, providing channel partners in South EMEA with reliable, supported solutions from world-leading hardware and software vendors.