
TOPIA
Protects your installed operating systems and third-party software from vulnerabilities.

Get a vulnerability assessment and remediation with one single platform that analyzes, prioritizes, and remediates cyber threats before they’re exploited.
TOPIA is a unified, cloud-based, and cost-effective solution that goes beyond traditional vulnerability management to actively identify security breaches and eliminate threats.
Let Vicarius provide you efficient and automated vulnerability remediation.

Visibility. Usability. Stability. With effortless deployment and an easy-to-use interface, TOPIA is designed to be intuitive for anyone involved in your organization’s security cycle.

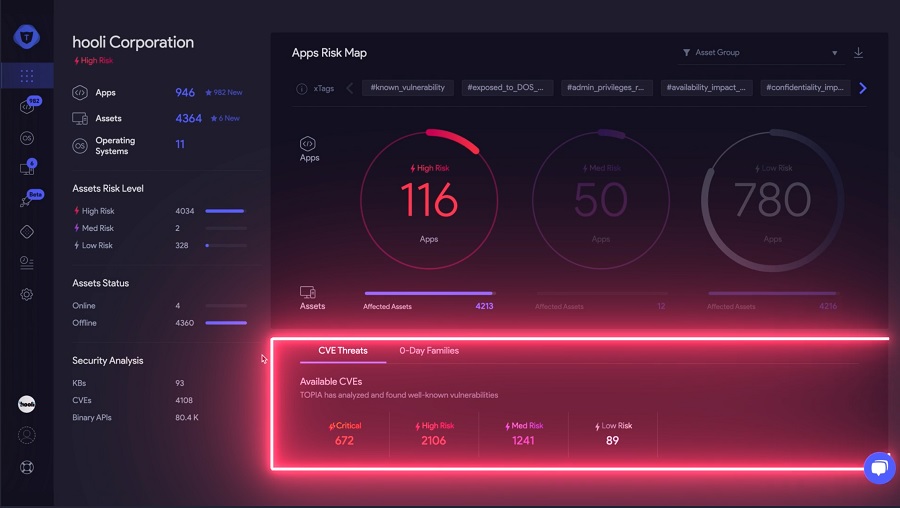
TOPIA is a consolidated vulnerability management platform that protects assets in real time. Its rich, integrated features efficiently pinpoint and remediate the largest risks to your cyber infrastructure. Resolve the most pressing threats with efficient automation features and precise contextual analysis.
Consolidate your software vulnerability assessment with one single TOPIA agent.
Let TOPIA do the work so you can focus on and remediate the threats that matter most.

Asset Inventory
Accurate knowledge is key for effective cybersecurity, so take control of your organization’s digital footprint with TOPIA. Get an exhaustive cloud-based, adaptive catalog of active servers, workstations, installed applications, and operating systems. Know what’s going on with real-time asset activity analysis for on-premise and cloud environments. Managing assets at any scale couldn’t be easier.

Prioritization with Context and Threat Analysis
Focus on vulnerabilities that have a real probability of being exploited instead of solving problems that don’t exist. TOPIA prioritizes software vulnerabilities using CVSS base metrics and an AI-based contextual usage risk-scoring engine. Get comprehensive coverage of your digital environment’s security status with a contextual and personalized threat analysis.

Patch Management
Integrated patch deployment tools cover Microsoft, Linux, MAC and 3rd party applications from the same dashboard to efficiently target all risks. TOPIA allows you to quickly test and install patches across your organization’s assets while maintaining transparency between departments. Plan ahead with scheduled one-time or recurring patches. Equip your IT and cybersecurity teams with the tools they need to work together and succeed.

Patchless Protection
TOPIA’s Patchless Protection™ deploys a force field around your most vulnerable assets using in-memory protection. TOPIA ensures your assets are always protected, even when a patch has not yet been prepared, tested, or deployed. Stay ahead of a security breach with TOPIA’s Patchless Protection™.

Auto-Actions
Threats don’t take time off, but Auto-Actions empower you to respond and mitigate threats automatically. With Auto-Actions, you can update individual or groups of assets automatically, you can deploy patches automatically based on severity, you can even set scripts to run anytime in response to triggering factors.
Prediction
TOPIA’s 0-day analysis engine automatically characterizes exploited areas in any binary software. Leveraging this knowledge, TOPIA identifies similar vulnerabilities in your applications, analyzes them, and informs you about potential weaknesses before hackers find them.


Multiple Threats.
One Solution!
TOPIA analyzes vulnerabilities, prioritizes threats, and protects vulnerable assets in real-time so your team can focus on getting more done.

- Auto Recognition
- App Real-time Threat Analysis
- Asset Real-time Threat Analysis

- Auto Recognition
-
App Real-time Threat Analysis
- Asset Real-time Threat Analysis

- App & OS Auto Recognition
- App Real-time Threat Analysis
- Asset Real-time Threat Analysis






