
END TO END SECURITY FOR
PRIVILEGED ACCESS

Eliminate Privileged Account Sprawl
Identify unmanaged, or unknown, privileged accounts with constant scanning. Stop attackers moving laterally in your environment by disabling unnecessary accounts.
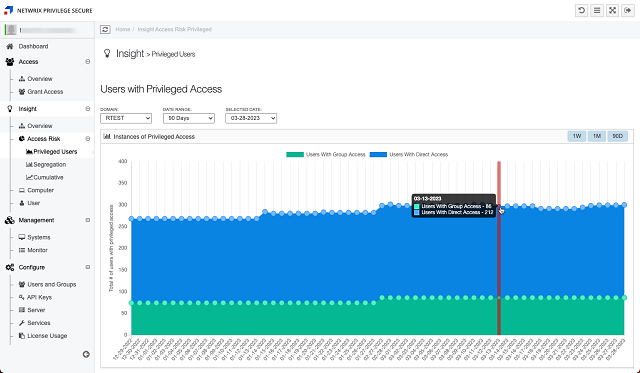
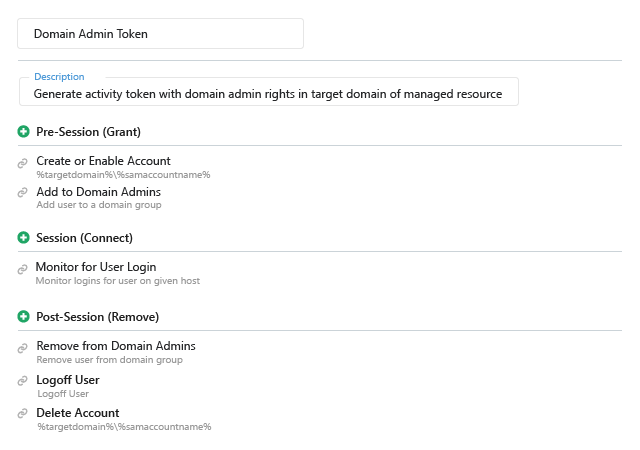
Secure Access to Privileged Accounts
Reduce security risk with zero standing privilege, secure credentials, and granular session monitoring.
Ensure Least Privileges on Endpoints
Prevent the risk of malware, ransomware, and noncompliance by delegating only the permissions standard users need, not local admin rights.
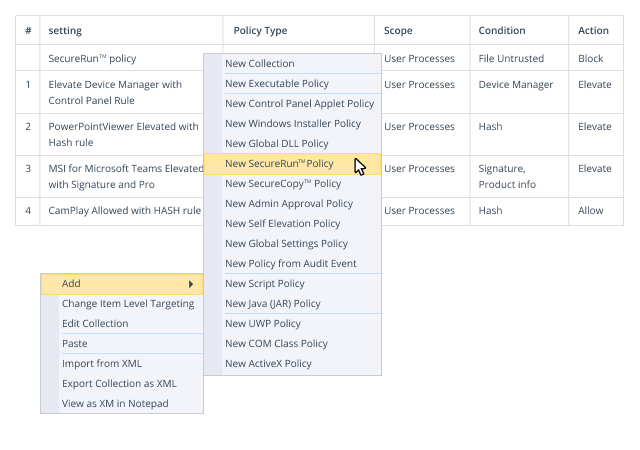
Slash the risk of compromise or misuse of privileged accounts
Kill standing privilege
Shrink your attack surface by eliminating standing privilege. Instead, create temporary accounts with just enough access to perform the task at hand and remove them when the job is complete.
Control sessions in real time
Raise the bar of accountability by monitoring all admin activities in real time across multiple IT systems. Observe sessions and stop suspicious activities at once.
Safeguard service accounts
Protect service accounts by rotating their passwords from one place; receive an alert if the process is disrupted, so you can pause it and roll back any unwanted changes.
Support investigations with video recordings
Easily review and search through recordings of completed sessions and provide solid evidence for compliance or security investigations.
Respond to auditor’s questions painlessly
Be prepared to quickly and definitively show who approved each privileged session, exactly what activity occurred during it, and whether any local groups or critical files were changed.
Bring your own vault®
Secure privileged accounts on your terms. Integrate Netwrix Privilege Secure with your current vault or use ours to store any privileged credentials that need to exist.






