
Webinar SealPath
Get Smart Data Protection with SealPath We’d like to personally invite you to our upcoming event, “Get Smart Data Protection, Tracking and Control against data
Leading Regional VAD Cyber Security and
IT distributor supporting local Channel Partners









Get Smart Data Protection with SealPath We’d like to personally invite you to our upcoming event, “Get Smart Data Protection, Tracking and Control against data
Webinar On-Demand Identify potential weaknesses before hackers find them Join experts from Vicarius and Multipoint Group to learn how to efficiently reduce Vulnerability Exposure and

Join Our Upcoming Webcast Acronis Cyber Protect November 24th – 11:00 CET Save Your Seat » Are your current solutions leaving gaps in your cyber

The Video is coming soon… Speakers: Ricardo Resnik CEO Multipoint Group Gabriel Popescu Solutions Engineer Acronis Join Our Upcoming Webcast Acronis Webinar – MSPs Can

Join Our Upcoming Webcast Vicarius Webinar – Visibility and Remediation July 27th – 11:00pm Join experts from Vicarius and Multipoint Group to learn how to

360-degree Prevention: Mailfor on-premise email and cloud email services WebBlock malware penetration via internet downloads and web content DevicesNeutralize malicious files located on external drives,

Speakers: Yonatan Goldshlager Presales Engineer Multipoint Group Shelly Raz Sales Manager Multipoint Group Enforce your corporate security policies at highest granularity: • Define and enforce
Join Our Upcoming Webcast Secure Single Sign-On May 25th – 14:00pm Save Your Seat » Today, the proliferation of digital access has made the world

Join Our Upcoming Webcast Catch Threats Others Miss with X-Ray Vision for Malware May 11th – 11:00am Save Your Seat » Organizations breached by advanced malware
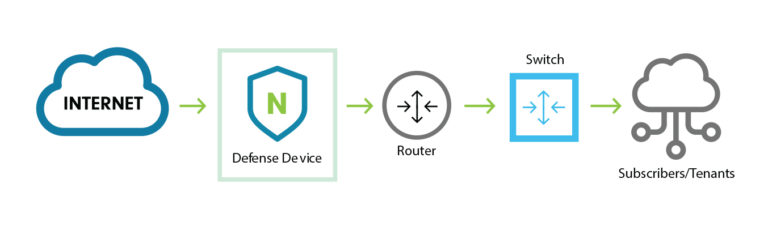
In recent weeks the Ukrainian Army and some major banks were subject to DDoS attacks. These attacks aim to severely impair and disrupt critical business

If you manage IT systems, it probably won’t come to you as big surprise, that according to a new research by Yubico 75% of enterprise

During the last 12 months, as demand for remote support peaked to new levels, AnyDesk became much more than an everyday working tool for IT: it became a vital enabler for collaboration, keeping office work flowing from home.

Garland adds robust network visibility solutions to Multipoint Groups’ Monitoring offering; Corero brings real-time automatic DDoS attack protection to the Protection solutions portfolio. Multipoint Group,
Tuesday, 19th January 2021.- Ingecom, Value Added Distributor (VAD) specialised in Cyber Security and Cyber Intelligence Solutions, and MultiPoint Group, Value Added Distributor expert in Cyber Security and IT Solutions, have signed a strategic alliance
The Multipoint Group, is a leader in Cyber Strong Strategy solutions, has announced a new branch in the Middle East region. The branch will operate
Multipoint GROUP is a leading distributor of IT security and Internet technology solutions, providing channel partners in South EMEA with reliable, supported solutions from world-leading hardware and software vendors.