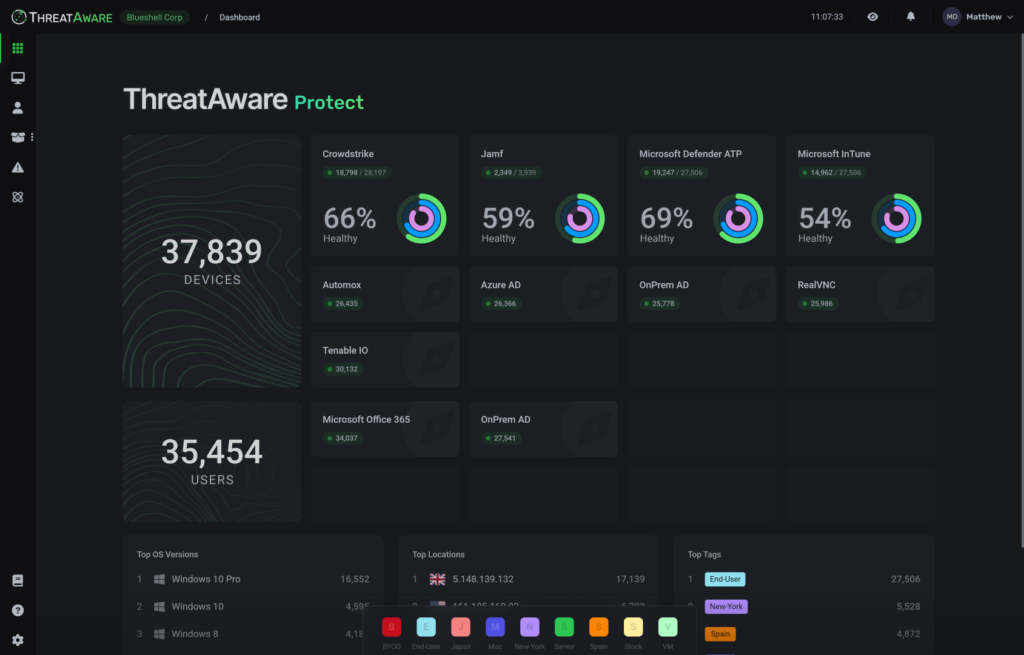
Connect to your existing endpoint security tools via API, and validate that they are correctly deployed, functioning and healthy across every device.
Cyber Asset Management. Simplified.
Connect to your existing endpoint security tools via API, and validate that they are correctly deployed, functioning and healthy across every device.
Connects to all your existing tools
ThreatAware continually polls your existing tools to detect every device and ensures all fundamental security controls are deployed, functioning and healthy.
Powerful Simplicity.
Automated Defence
When issues arise the workflow automation engine can trigger actions via a webhook.
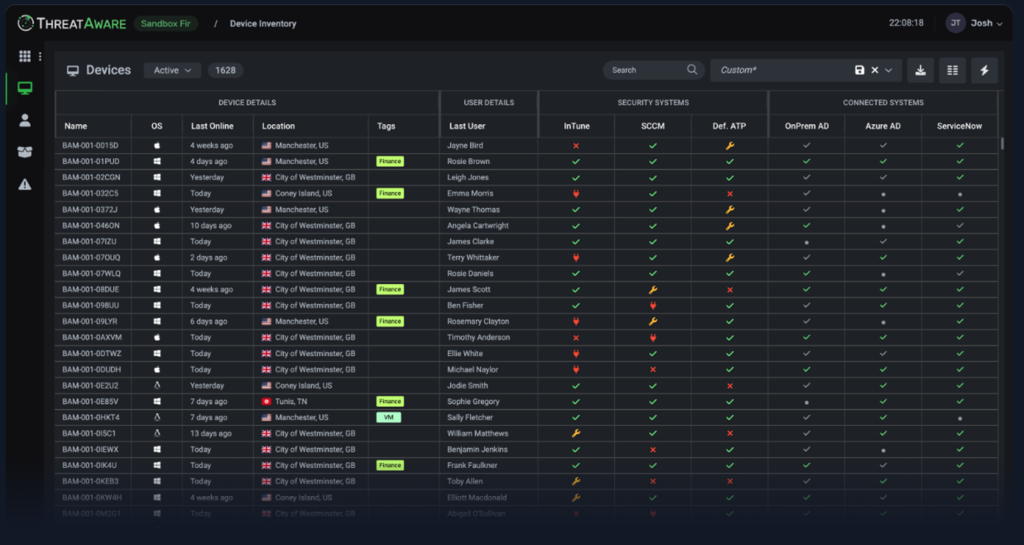
Create a highly accurate device inventory by connecting to your existing systems via API.
Stop alert fatigue.
Stop alert fatigue. When your monitoring systems accurately depicts your live environment, every alert is real.
Dynamic Tagging.
Dynamic Tagging. Generated from any field from a device. Allows you to quickly group your cyber assets for monitoring and configuration purposes.
Security Control Health.
Security Control Health. Gain a macro view of your security control health regardless of how many controls you are monitoring.
See how the world’s most innovative organisations use ThreatAware to manage vast and complex IT environments.
Work faster
A better way
In the era of cloud software and remote working, ThreatAware is the only way to make sure every endpoint in your organisation is legitimate and protected. Our comprehensive, fully-automated asset inventory uncovers every device accessing company data.