
YubiHSM
Game changing cryptographic protection for servers, applications and computing devices
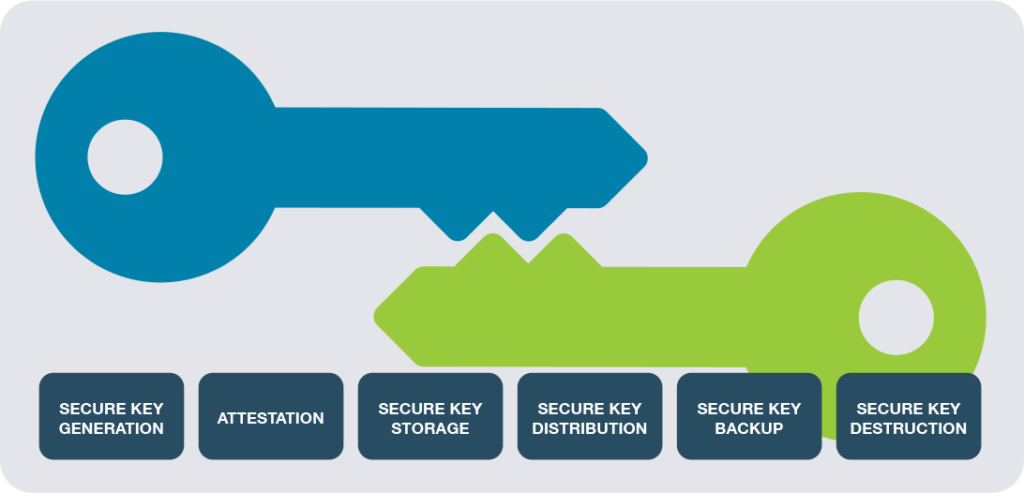
● Secure key storage and operations on tamper-resistant hardware, with audit logging
● Extensive cryptographic capabilities including hashing, key wrapping, asymmetric signing, decryption, attestation and more
Cryptographic keys stored in software can be copied, and are vulnerable to accidental distribution and remote theft.
Without strict procedures, it is easy for admins or malicious insiders to backup keys to USB flash drives, FTP them, or share to others via a cloud storage service. Additionally, sophisticated attackers can gain admin access or deploy trojan malware that installs on servers, searches for cryptographic keys, and then copies them for sale on dark web sites like Alphabay
The hardware-based YubiHSM 2 enables secure key storage and operations by preventing accidental copying and distribution of keys, and by preventing remote theft of keys stored

Simplified deployment for organizations of all sizes
Ultra portable form factor at an affordable price secures a wide range of long-standing and emerging use cases
Rapid integration with hardware-backed security
A comprehensive cryptographic open source toolbox with support for PKCS#11

Enhanced protection for cryptographic keys
Secure generation, storage and management of digital keys
The world’s smallest HSM secures modern infrastructures

YubiHSM highlights:
- Portable nano form factor with low-power usage
- Secure key storage and crypto operations on a tamper-resistant device
- Network shareable for use by applications on other servers
- Interfaces via YubiHSM KSP, PKCS #11 and native libraries
- Direct USB support beneficial for virtualized environments

Enhanced protection for cryptographic keys
Prevent poor cryptographic key handling by preventing accidental copying and distribution of cryptographic keys.
Defend against remote attacks and eliminate remote extraction of private keys by storing cryptographic keys securely on hardware
Strong hardware-based security ensures highest bar for protection of sensitive information and data
Rapid integration with hardware-backed security
Open source SDK enables rapid integration
Frees developers to easily build support for hardware-based strong security into a wide array of platforms, applications and services
Enables organizations to easily make the YubiHSM 2 features accessible through industry standard PKCS#11
Simplified deployment for organizations of all sizes
Ultra-portable and fits easily into a front USB slot on computers and servers
Secures modern use cases such as cryptocurrency exchanges, IoT gateways and proxies and cloud services
Secures Microsoft Active Directory certificates






